The average cost of a data breach reached $4.88 million in 2024, yet only 30% of companies have deployed access control systems to protect their physical security. As hybrid work models create fluctuating occupancy patterns and modern security threats become more sophisticated, you can no longer rely on traditional lock-and-key systems to protect your people, data, and assets.
With the global access control market projected to reach $25.15 billion by 2034, organizations that invest in these systems now position themselves ahead of evolving security challenges.
Understanding physical access control systems
A physical access control system (PACS) is an electronic system that controls the ability of people or vehicles to enter a protected area through authentication and authorization at access control points. Unlike security measures that rely on security guards or physical keys, modern access control systems integrate hardware, software, and networking components to create intelligent, scalable security solutions.
These systems serve as the digital gatekeepers of your workplace, managing who can gain access to specific areas, when they can enter, and maintaining detailed logs of all access attempts. According to NIST, these systems authenticate and authorize access through various credential types, from traditional key fobs to advanced mobile credentials, electronic ID badges, and biometric scanners.
The sophistication of access control solutions extends beyond door locks. Modern systems can integrate with visitor management systems, video security cameras, and alarm systems to create comprehensive security ecosystems that adapt to your organization's unique requirements.
Core components of effective access control systems
Physical access barriers and control points
At the foundation of any access system are the physical barriers where authentication occurs. These include locked doors, turnstiles, security gates, and other entry points that regulate access.
Electronic access control points can verify user credentials, deny or grant access based on permissions, and maintain detailed logs of all access attempts. Each control point connects to the central system, creating a network of monitored entry and exit points.
Modern access control models accommodate different authentication methods, from proximity cards and key fobs to mobile credentials. This flexibility lets companies implement security measures that match their needs while maintaining comprehensive access monitoring.
User credentials and authentication methods
Access credentials are the cornerstone of any access control system. Traditional physical keys have largely given way to more sophisticated credential types that offer enhanced security and administrative flexibility. Key fobs and proximity cards remain popular choices, providing reliable authentication while maintaining ease of use for daily operations.
Mobile access control has emerged as a compelling solution, allowing employees to use their smartphones to gain building access. This approach eliminates the need to manage physical cards while providing heightened security.
Biometric identification is the cutting edge of access credential technology. Fingerprint recognition systems lead the adoption, with 44% of consumers ranking them as the most secure authentication method. Meanwhile, facial recognition and iris scanning technologies offer touchless alternatives that align with hygiene concerns.
Access control software and management systems
The access control dashboard serves as the security command center, providing system administrators with tools to manage authorized users and credentials, monitor access attempts, and generate security reports. This software enables granular permission management, allowing companies to create access models tailored to their specific needs.
Cloud-based systems have revolutionized how companies manage security across multiple locations. These platforms provide centralized management capabilities while reducing the infrastructure requirements. According to NIST research, 70% of organizations are expected to adopt cloud services for their access control needs.
Integration capabilities are another critical aspect of access control software. The most effective systems can connect with existing systems, including video management systems, alarm systems, and workplace management platforms, to create unified security dashboards.

Learn the workplace security benefits of implementing a visitor management system and integrating it with access control systems.
Read more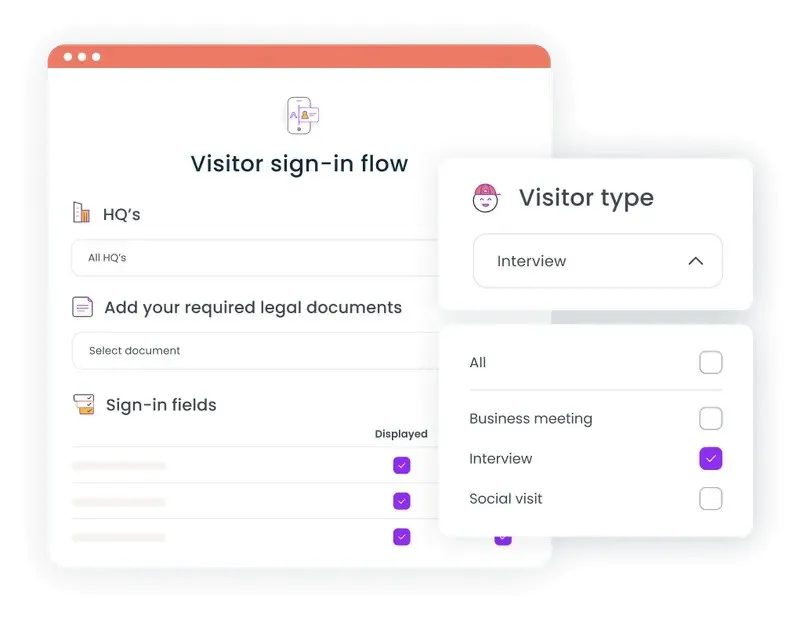
Key benefits of physical access control security
Enhanced security and threat prevention
Access control systems provide multiple layers of security that traditional methods cannot match. By requiring authentication at every access point, these systems create audit trails that help security teams identify potential threats and investigate security breaches. Workplace violence incidents affected 57,610 employees between 2021 and 2022, showing the importance of controlling who can gain entry to your workplace.
Modern systems excel at preventing unauthorized entry through sophisticated authentication. Multi-factor authentication, combining physical credentials with PIN codes or biometric verification, creates multiple barriers that potential intruders must overcome.
Real-time monitoring and incident response
The ability to monitor access attempts in real-time transforms how companies respond to security incidents. Access control systems automatically alert security personnel when unauthorized access attempts occur, enabling immediate response. Integration with video security cameras provides additional context for security teams, allowing them to verify the identity of individuals attempting access.
Emergency response capabilities are another benefit of access control technology. During emergencies, security teams can instantly secure specific areas or facilitate a controlled evacuation by remotely managing electronic locks.
Operational efficiency and cost savings
Automated access management eliminates the need for manual key distribution and retrieval, which is just one example of improved efficiency. Organizations that implement access control systems typically see significant cost savings through reduced administrative overhead and better operational efficiency.
Access control systems also provide valuable insights that inform real estate decisions. By tracking when and how employees use different areas of your facility, these systems help optimize space utilization and identify opportunities for cost savings. This data becomes particularly valuable for organizations managing hybrid work models with fluctuating occupancy patterns.
Create a seamless visitor experience while maintaining security with Gable's visitor management system.
Learn more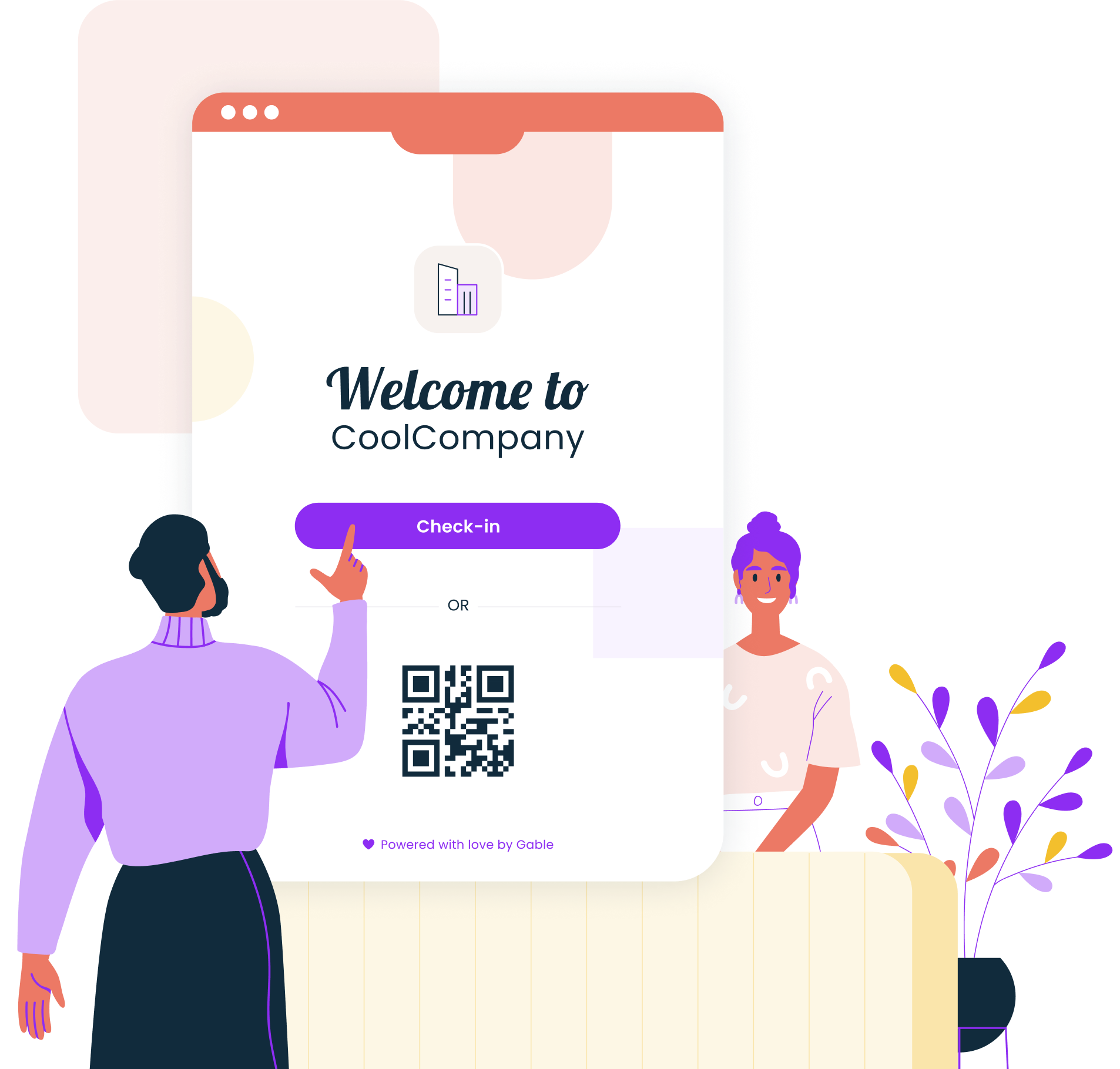
Workplace insights: What access control data reveals about your operations
Space utilization and occupancy patterns
Access control systems generate rich datasets that provide unprecedented insights into how your workplace functions. Access logs reveal peak usage times for different areas, helping facilities teams optimize everything from HVAC schedules to cleaning routines. This data proves especially valuable for organizations implementing hybrid work strategies, where understanding space usage patterns informs real estate decisions.
Occupancy tracking through access control enables more accurate space planning and resource allocation. Rather than relying on estimates, organizations can base real estate decisions on usage data. This helps identify underutilized areas that might be repurposed or right-size real estate footprints to match actual needs.
Security pattern analysis and risk assessment
Access control logs provide security teams with powerful tools for identifying potential risks and investigating incidents. Unusual access patterns—such as after-hours entry attempts or unauthorized access to sensitive areas—can indicate potential security threats or policy violations that require investigation.
The data also enables security improvements through pattern analysis. By understanding how legitimate users typically access facilities, security teams can fine-tune alert thresholds and access policies to strike a balance between security and efficiency.
Compliance reporting and audit preparation
Many industries require detailed access logs for regulatory compliance and audit purposes. Access control systems automatically generate the necessary documentation for compliance reporting.
Automated reporting capabilities transform audit preparation from a time-intensive process into a streamlined digital workflow. Access control systems can generate detailed reports that show who accessed specific areas, when access occurred, and whether the access was authorized. This documentation proves essential for demonstrating compliance with industry regulations and security standards.
Choosing the right access control solution: 5 key considerations
1. Assess your security requirements and risk profile
Begin by conducting a comprehensive security assessment that identifies your organization's specific risks and requirements. Consider factors such as industry regulations, the sensitivity of information stored on-site, and the types of threats your organization faces. Healthcare organizations, for example, face average data breach costs of $10.93 million, making robust access controls essential for protecting patient information.
Evaluate your current security gaps and consider how access control systems can address these vulnerabilities. Organizations handling sensitive information may require advanced authentication methods and detailed audit trails, while others might prioritize ease of use and integration with existing systems.
2. Plan for scalability and future growth
Select access control systems designed to grow with your organization. Cloud-based solutions offer particular advantages for scalability, allowing you to add new locations or users without significant infrastructure investments. Consider how the system will accommodate potential changes in your workforce size, facility footprint, or security requirements.
3. Evaluate integration capabilities with existing systems
Modern workplaces rely on multiple interconnected systems, making integration capabilities essential for any access control solution. Evaluate how well potential systems can connect with your existing tech stack, including video surveillance, alarm systems, and workplace management platforms.
Visitor management systems are a particularly important integration. Effective access control models combine employee access management with visitor tracking and authentication. This approach provides complete visibility into who is present in your facility.
4. Consider user experience and adoption
The most sophisticated access control system provides no value if employees find it difficult or frustrating to use. Evaluate the user experience from both employee and administrator perspectives, considering factors such as authentication speed, credential management, and system reliability.
Mobile access control has gained popularity partly due to its familiar user interface, as most employees already understand how to use smartphones. This familiarity can significantly reduce training requirements and improve adoption rates.
5. Review compliance and reporting capabilities
Ensure your access control system can meet current and future compliance requirements for your industry. Many organizations must demonstrate compliance with standards such as SOC 2, HIPAA, or GDPR, requiring detailed access logs and reporting capabilities.
Automated compliance reporting capabilities can reduce the administrative burden associated with audit preparation and regulatory reporting. Look for systems that can generate the reports and documentation required for your industry's compliance standards.
Integration with visitor management systems
Unified access control and visitor tracking
The integration of access control systems with visitor management systems creates a comprehensive security ecosystem that addresses the needs of both employees and visitors. Rather than managing separate systems for different types of building occupants, integrated solutions provide unified visibility and control.
This integration enables sophisticated access scenarios, such as automatically granting temporary access permissions to pre-registered visitors or requiring escort protocols for certain types of guests. Modern visitor management systems can integrate with access control to create seamless experiences for guests while maintaining strict security standards.
Enhanced security protocols for mixed environments
Hybrid workplaces often host a diverse range of visitors, including job candidates, business partners, contractors, and delivery personnel. Integrated access control and visitor management systems enable organizations to implement security protocols based on visitor type and purpose.
For example, contractors may receive extended access permissions for project work areas, while job candidates receive limited access that requires escort protocols. This granular control ensures that security policies align with the actual risk profiles of different visitor types, while maintaining operational efficiency.
Streamlined compliance and reporting
Integrated systems simplify compliance reporting by providing unified access logs that include both employee and visitor activity. This comprehensive view proves essential for organizations that must demonstrate facility security controls for regulatory compliance or audit purposes.
The integration also enables more sophisticated analytics, combining employee access patterns with visitor traffic data to provide utilization insights. This holistic view supports better decision-making around space planning, security policies, and operational efficiency improvements.
Gable's visitor management system integrates with physical access control to provide both strong security and a seamless visitor experience.
Get a demo





.svg)





.svg)

























