Workplace security is evolving beyond traditional lock-and-key systems. With data breaches costing an average of $4.88 million and 62% of businesses allocating more resources to workplace protection in 2024, organizations need comprehensive security strategies that address physical threats, cybersecurity risks, and visitor management.
Workplace security has become a business imperative. As hybrid work models reshape office environments and security threats grow more sophisticated, protecting employees, visitors, and sensitive information requires a strategic, multi-layered approach.
The average cost of a data breach reached $4.88 million in 2024, a 10% increase from the previous year. Meanwhile, 62% of businesses plan to allocate more resources to workplace protection, recognizing that security failures can devastate operations, damage reputation, and result in massive financial losses.
Understanding modern workplace security challenges
With 68% of companies adopting hybrid work models, organizations face evolving vulnerabilities ranging from unauthorized office access to cyber threats targeting distributed teams.
Fluctuating occupancy levels create blind spots that manual processes struggle to manage. Research shows that 33% of companies still manage over half of their operations manually, creating inefficiencies that can cost them up to 30% of their revenue annually. These processes hinder the ability to track visitor patterns, identify unusual access attempts, or respond quickly to security incidents.
The threat landscape itself has intensified. Physical security incidents increased for 28% of organizations, while 87% predict that physical security incidents will either increase or remain at current levels through 2024. These incidents encompass everything from unauthorized access and theft to workplace violence and data breaches that compromise sensitive data.

Upgrade your office security approach with data-driven insights. Discover the strategies leading organizations use to protect their people and assets without compromising productivity.
Read our guide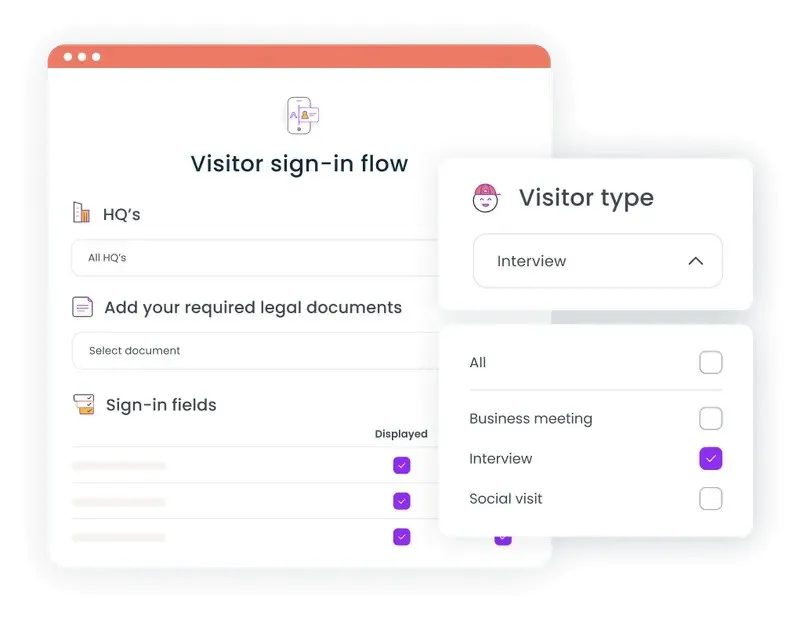
The convergence of physical and digital threats
Modern workplace security threats rarely exist in isolation. About 40% of all data breaches involve information distributed across multiple environments, highlighting how physical and digital vulnerabilities often intersect. Cybercriminals combine digital attacks with physical infiltration tactics, making unified security approaches essential.
For instance, a seemingly simple unauthorized building access can lead to compromised network connections, stolen devices, or direct access to sensitive systems. This requires the right security measures that address both domains rather than treating them as separate concerns.
Workplace security measures every organization needs
The most effective approaches combine tech solutions with clear workplace security policies and employee training to protect against security threats.
Access control systems: Your first line of defense
Modern access control systems have evolved to include mobile credentials, biometric systems, and cloud-based management platforms that provide better control over physical access to your workplace.
Badge systems remain one of the most effective and easiest security measures to implement. Employees use key cards, mobile apps, or ID badges to gain physical access to specific areas based on their role and authorization level. Advanced access control technology can restrict access by time, location, or purpose while providing real-time data about building occupancy and space utilization that helps optimize your workplace strategy.
The integration of access control technology with other workplace systems creates additional security benefits. When connected to space management software, these systems provide valuable insights into how employees use office spaces, which can inform both security policies and real estate decisions.
Visitor management systems: controlling who enters your workplace
A robust visitor management system ensures that only authorized personnel access your workplace while creating a professional experience for legitimate guests. Modern visitor management systems replace traditional paper sign-in sheets with digital platforms that can screen visitors, print temporary badges, and maintain detailed access logs for security guards to monitor.
Key features of effective visitor management include blocklist screening against custom and third-party databases, automatic host notifications when visitors arrive, and integration with existing alarm systems. These capabilities help prevent unauthorized access while streamlining the check-in process for approved visitors and ensuring occupational safety compliance.
The global visitor management system market reached $1.63 billion in 2023 and is projected to grow at a 13.4% compound annual growth rate through 2030, reflecting the increasing recognition of visitor management as a critical security component. Organizations implementing these systems report improved security effectiveness and better ability to protect employees from potential threats.
Surveillance systems and monitoring technology
Security cameras and monitoring systems provide crucial visibility into workplace activities and serve as both deterrents and investigative tools for security issues. However, effective surveillance goes beyond simply installing cameras—it requires strategic placement, proper recording capabilities, and integration with other security systems to create comprehensive workplace safety.
Modern surveillance systems incorporate artificial intelligence to detect unusual behavior patterns and automatically alert security personnel to potential security breaches. These systems can identify unauthorized access attempts, monitor high-traffic areas, and provide valuable evidence in case of security incidents or workplace injuries that require investigation.
When implementing surveillance technology, organizations must balance security needs with employee privacy expectations and comply with applicable regulations regarding workplace monitoring. Successful implementations focus on protecting physical assets while maintaining employee trust and preventing unauthorized access to sensitive areas.
Protecting digital assets and sensitive information
Cyber attacks are an increasingly critical component of workplace security. With 82% of data breaches involving cloud-stored information and 68% involving human elements, organizations must address both technological solutions and human factors to protect private data and intellectual property.
Data security fundamentals
Protecting sensitive data requires implementing multiple layers of security controls and password protection tools. Data encryption ensures that information remains protected even if digital systems are compromised, while secure passwords and multi-factor authentication prevent unauthorized access to digital assets and company data.
Organizations should implement comprehensive data classification systems that identify sensitive information and apply appropriate protection measures based on data value and risk levels. Regular security audits help identify potential security breaches before they can be exploited by malicious actors seeking to steal digital assets or compromise network traffic.
Network security and remote work considerations
The shift toward hybrid work models introduces additional cybersecurity challenges and potential digital threats. Remote workers often access company systems from less secure environments, potentially exposing sensitive information to new risks and cyber threats that could compromise intellectual property.
A virtual private network provides essential protection for remote workers by encrypting data transmission between remote devices and company networks. However, VPN implementation must be coupled with endpoint security measures and regular training sessions to maintain effectiveness against increasingly sophisticated attack methods.
Organizations should also consider implementing zero-trust security models that verify every access request regardless of location or device. This approach assumes that potential threats can originate from anywhere and requires continuous verification of user identity and device security to prevent security breaches. Effective hybrid work strategies integrate security measures with operational flexibility to support distributed teams without compromising protection.
Developing comprehensive security policies and procedures
Technology alone cannot ensure workplace security: organizations must establish clear security policies and procedures that guide employee behavior and response protocols. Effective security policies address both routine operations and emergencies.
Creating security awareness through training
Employee training represents one of the most cost-effective security investments organizations can make. Research indicates that 88% of cybersecurity breaches are caused by human error, making security awareness training sessions crucial for reducing risk and improving workplace security across all business operations.
Training sessions should cover common threats such as phishing attempts, social engineering tactics, and physical security risks that could lead to workplace violence or unauthorized access. Regular training helps ensure that employees stay current on emerging security threats and understand their role in maintaining workplace safety and protecting against potential security threats.
Interactive training approaches, including simulated phishing exercises and tabletop emergency drills, provide practical experience that helps employees recognize and respond appropriately to security threats. Small businesses particularly benefit from these cost-effective training methods that don't require expensive technological solutions.
Emergency response and incident response plan
Comprehensive security planning includes detailed emergency response procedures that address various threat scenarios and potential security incidents. These procedures should clearly define roles and responsibilities, communication protocols, and escalation processes for security personnel and all employees to follow during critical situations.
Regular testing of emergency procedures through drills and simulations helps identify gaps in planning and ensures that employees can respond effectively under stress. Documentation of these procedures should be easily accessible and regularly updated to reflect changes in security threats or organizational structure, particularly for companies managing multiple physical premises.
An effective incident response plan should also include coordination with local law enforcement and emergency services, as well as protocols for communicating with employees, customers, and stakeholders during security incidents. This comprehensive approach helps organizations maintain business continuity while protecting people and assets.
Enhance workplace security with Gable's visitor management solution. Protect your workplace, welcome guests, and gain valuable insights while maintaining compliance.
Learn more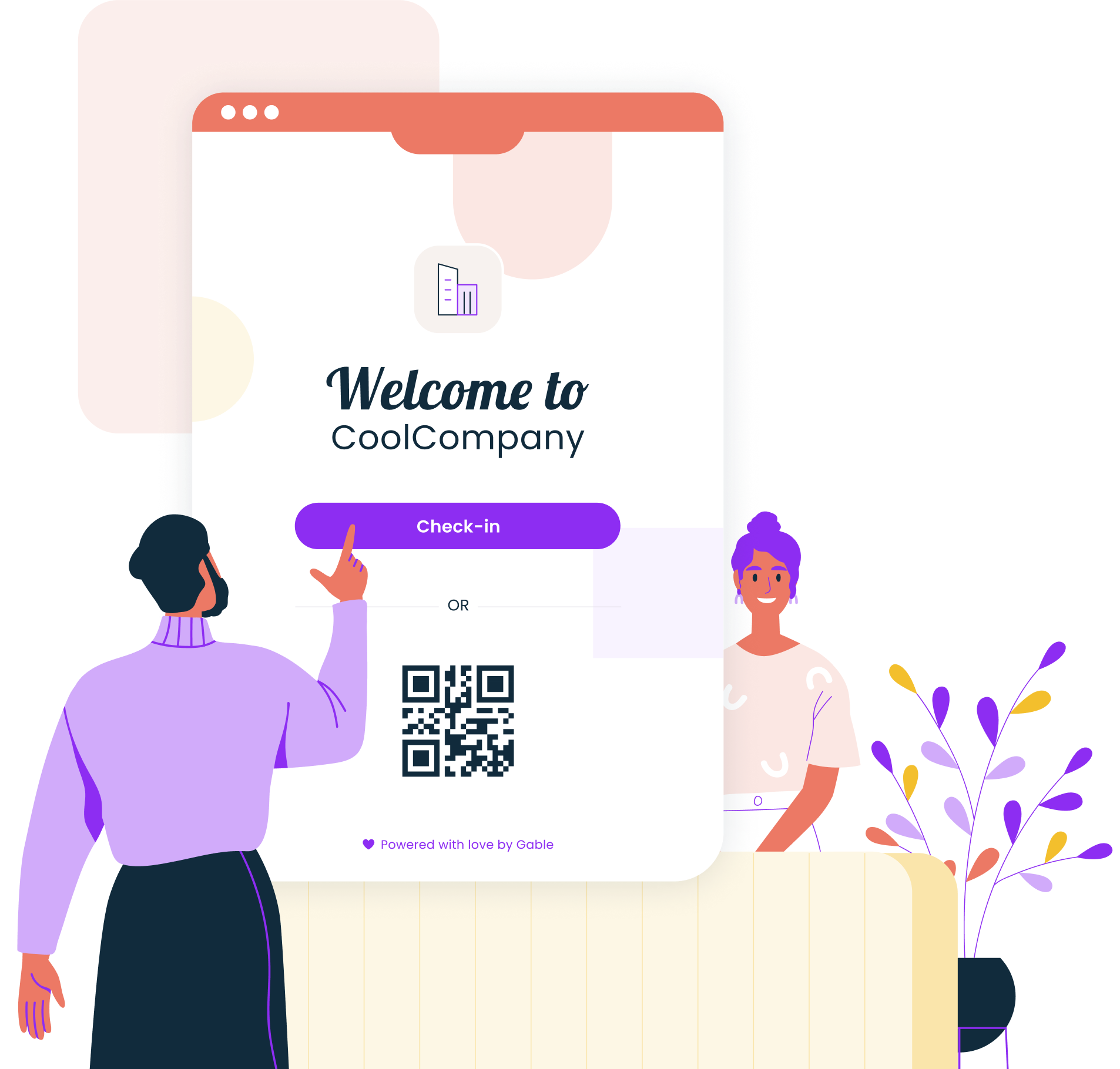
How to implement security technology
Successful security implementation requires careful planning and consideration of how different technological solutions work together. The most effective approaches focus on integration rather than deploying multiple standalone systems that create security gaps and inefficiencies in protecting physical assets.
Integration and interoperability
Modern workplace security systems work best when they can share information and coordinate responses to security issues. Integrated platforms that combine visitor management, access control, and surveillance systems provide comprehensive security coverage while reducing administrative overhead and improving security effectiveness.
Open-standard technologies facilitate easier integration with existing systems and provide flexibility for future upgrades. Organizations should prioritize solutions that can adapt to changing needs rather than requiring complete system replacements as requirements evolve, particularly when implementing robust security measures across multiple locations.
Cost considerations and return on investment
Security investments should be evaluated based on both direct costs and potential risk mitigation benefits. While advanced security systems require upfront investment, the cost of security incidents—including data breaches, theft, and operational disruptions—often far exceeds prevention costs, making prioritizing workplace security a sound business decision.
Organizations can optimize security spending by focusing on solutions that address multiple security requirements simultaneously. For example, visitor management systems that integrate with access control and provide space utilization data offer value beyond security alone, helping business leaders make informed decisions about their workplace security plan and regulatory compliance requirements.
Regular risk assessment helps companies identify critical vulnerabilities and prioritize investments for maximum risk reduction. This systematic approach ensures that limited security budgets are allocated to address the highest-priority threats and protect employees most effectively.
Measuring and improving security effectiveness
Effective security management requires ongoing measurement and continuous improvement to address evolving security threats. Organizations should establish key performance indicators that track both security metrics and operational efficiency while ensuring all security measures meet the right security standards for their industry.
Security metrics and monitoring
Important security metrics include incident response times, access control effectiveness, visitor processing efficiency, and employee compliance with security procedures. Regular analysis of these metrics helps identify trends and areas for improvement in protecting against potential security breaches and maintaining workplace safety.
Automated reporting capabilities in modern security systems provide real-time visibility into security performance and can alert managers to potential security issues before they become serious problems. This proactive approach helps prevent unauthorized access and ensures that security personnel can respond quickly to emerging threats.
Compliance and regulatory compliance
Many industries have specific regulatory requirements for workplace security, visitor tracking, and data protection that directly impact how organizations implement security measures. Organizations must ensure that their security measures meet applicable compliance standards while supporting operational efficiency and protecting against potential security threats.
Regular compliance audits help identify potential gaps and ensure that security procedures remain current with changing regulations. Documentation of security measures and incident responses supports compliance efforts. It provides evidence of due diligence in case of regulatory review, particularly important for protecting sensitive information and maintaining trust with stakeholders.
The future of workplace security
Workplace security continues to evolve as new technologies emerge and threat detection becomes more sophisticated. Organizations that stay informed about security trends and adapt their approaches accordingly will be better positioned to protect their people and digital assets from increasingly sophisticated cyber threats.
Emerging technologies and trends
Artificial intelligence and machine learning are increasingly integrated into security systems to provide predictive analytics and automated threat detection. These technological solutions can identify patterns that human observers might miss and respond more quickly to potential threats, helping protect employees and prevent security incidents.
Biometric systems are becoming more sophisticated and widely adopted, offering higher security levels than traditional access methods. These systems can provide both convenience and security by eliminating the need for key cards that can be lost or stolen, while providing more secure access to physical access points throughout the workplace.
Building resilient security cultures
The most effective workplace security approaches combine technology with strong security cultures that emphasize shared responsibility for safety and protection. Organizations that successfully engage employees in security initiatives typically experience fewer security incidents and faster threat detection, creating safer environments for everyone.
Regular communication about security topics, recognition of good security practices, and transparent reporting of security metrics help build employee engagement and awareness. When employees understand their role in maintaining security and feel empowered to report concerns, organizations benefit from an additional layer of protection against both physical and digital threats.
Gable's integrated workplace management platform includes visitor management, access control integrations, and space optimization tools that help you create a secure workplace.
Get a demo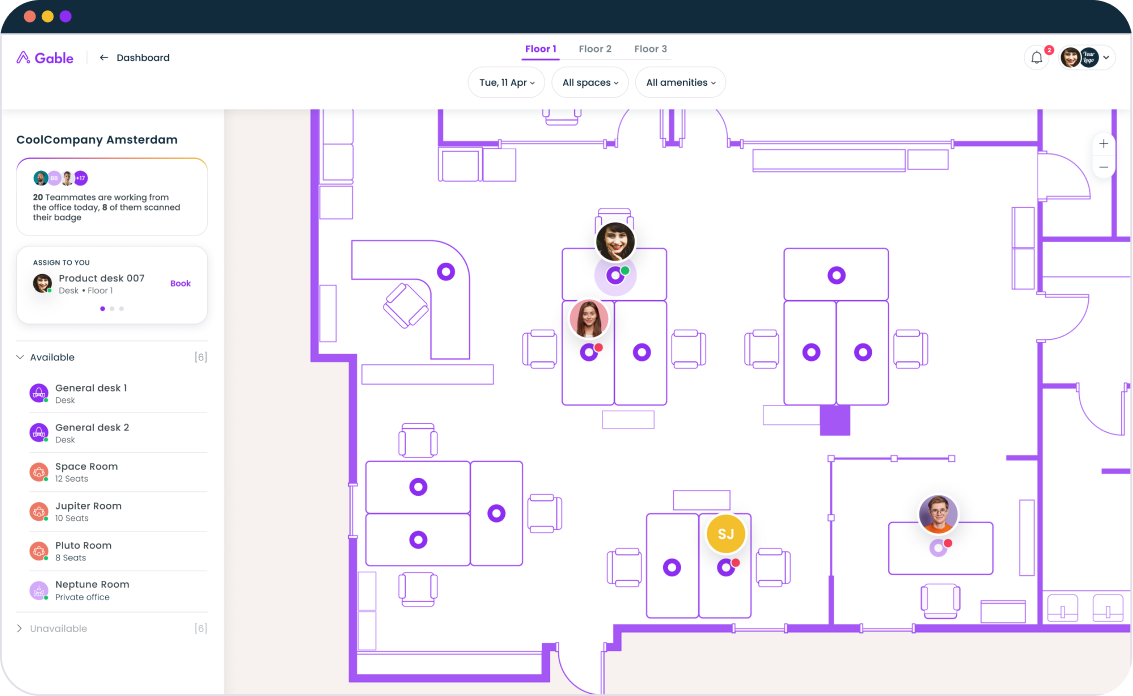





.svg)





.svg)
























