Modern workplace security extends far beyond traditional lock-and-key systems. The global average cost of a data breach reached $4.88 million in 2024, a 10% increase from 2023 and the largest annual spike since the pandemic. Meanwhile, physical security incidents continue rising, with organizations facing threats that target people, property, and sensitive data simultaneously.
For workplace leaders managing hybrid teams with fluctuating occupancy, the security landscape has fundamentally shifted. Traditional approaches cannot address the vulnerabilities created by distributed teams, unpredictable visitor traffic, and the convergence of physical and digital risks. This guide provides actionable strategies to implement robust security measures that protect employees and assets while maintaining operational efficiency.
What is office security?
Office security encompasses all policies, procedures, and technologies deployed to protect employees, visitors, physical assets, and sensitive information from internal and external threats. It addresses three interconnected domains:
- Physical security involves systems that safeguard the workplace environment, including surveillance cameras, access control systems, and intrusion detection that prevent unauthorized entry, theft, vandalism, and workplace violence.
- Digital security protects technology systems, networks, and data from cyber attacks, malware, and breaches. With 82% of data breaches involving cloud-stored information, organizations must secure data across multiple environments.
- Procedural security establishes clear rules, training sessions, and protocols that guide how employees and security personnel respond to various threats, from emergency response plans to visitor management procedures.
These domains frequently intersect. A digital access badge connects to a central database and adheres to specific usage policies. A visitor management system collects sensitive data that requires both physical and digital protection. The most effective security strategies recognize these connections and create integrated frameworks rather than isolated solutions.
Why office building security matters
Protecting employees directly impacts your ability to attract and retain talent. According to AlertMedia's research, 97% of employees consider workplace safety when choosing where to work. When team members feel secure, they focus on their responsibilities without worrying about potential risks to their well-being.
Effective security measures also deliver measurable financial benefits:
- Organizations using AI and automation in security operations save an average of $2.2 million per breach
- Security investments reduce insurance premiums and minimize legal liability
- Preventing disruptions protects productivity and operational continuity
Regulatory compliance adds another layer of urgency. OSHA requires workplaces to be free from recognized hazards, while GDPR and HIPAA mandate specific protections for visitor information and sensitive data. Organizations that violate compliance requirements face penalties exceeding $14 million, including fines, revenue loss, and reputational damage.
Essential office security best practices
Implement comprehensive access control systems
Modern access control systems form the foundation of effective physical security. These systems go beyond traditional keys to incorporate badge readers, biometric authentication, and mobile credentials. Strategic deployment restricts physical access based on role, time, and location.
Multi-factor authentication adds critical protection by requiring verification through multiple methods, such as presenting a badge and entering a PIN, or using biometric scanning in high-security zones. This layered approach significantly reduces the risk of unauthorized access, even if individual credentials are compromised.
Access control technology also provides valuable data for security operations:
- Detailed audit trails document who accessed which areas and when
- Integration with badge access control systems enables automated provisioning as employees join or leave
- Real-time monitoring supports both security investigations and compliance reporting
Deploy a modern visitor management system
Visitor management serves as your first line of defense against security breaches. Paper sign-in sheets cannot screen guests, track movements throughout premises, or provide immediate alerts when potential threats arise.
The business case is compelling: 74% of workplaces struggle with unauthorized visitors, and 28% report security breaches due to poor visitor management, with each incident costing an average of $1.2 million. A robust system prevents these breaches by screening visitors against watchlists, verifying identity through photo capture, and maintaining detailed visitor logs for security audits.
Modern systems streamline the guest experience while strengthening security:
- Pre-registration lets hosts invite visitors in advance, reducing wait times
- Automatic notifications alert employees when guests check in
- Badge printing provides visible identification on premises
- Integration with access control ensures visitors access only to approved areas
These capabilities protect your workplace's safety while creating positive first impressions.

74% of workplaces struggle with unauthorized visitors. See how guest management systems screen, track, and protect without slowing down your lobby.
Read the guide
Establish strategic surveillance systems
Surveillance cameras installed at key locations continuously monitor entry points, reception areas, storage facilities, and building perimeters. Research suggests visible security cameras may deter up to 60% of would-be intruders. Beyond deterrence, surveillance systems help security guards gather evidence and investigate incidents.
Modern surveillance goes beyond passive recording to include AI-powered analytics that automatically detect unusual behavior patterns, identify tailgating through secure doors, recognize abandoned objects, and send immediate alerts to security personnel. This proactive approach enables rapid response before minor issues escalate.
Balance security needs with privacy expectations by establishing clear policies about camera placement, footage storage, access permissions, and data retention. Transparent communication about surveillance practices helps maintain employee trust while protecting physical assets.
Strengthen cybersecurity and data protection
Cyber attacks represent the fastest-growing category of workplace threats. Credential-based attacks account for 16% of all breaches and take an average of 292 days to identify and contain, making them among the most expensive incidents organizations face.
Essential cybersecurity measures include:
- Password protection tools that help employees maintain unique, complex credentials across systems
- Multi-factor authentication that prevents unauthorized access even when passwords are compromised
- Regular software updates to patch vulnerabilities before attackers exploit them
- Antivirus software and firewalls that monitor for suspicious network activities
- Data encryption protects sensitive information in transit and at rest
For organizations with remote workers, mobile device management enforces security protocols on phones and tablets accessing company systems, helping teams stay protected regardless of location.
Develop comprehensive emergency response plans
Every workplace needs detailed emergency and evacuation plans that address various scenarios: natural disasters, fires, medical emergencies, active threats, and cyberattacks. Effective plans outline specific procedures, assign roles to security personnel, and include regular drills.
Emergency protocols should address how to account for all building occupants during evacuations. Visitor management systems prove invaluable here by providing real-time data about who is on-site, helping first responders ensure everyone reaches safety. Organizations with tested incident response teams see breach costs $1.5 million lower than those without prepared capabilities.
Establish relationships with local emergency services before incidents occur. Share building layouts, access procedures, and emergency contact information so responders can act quickly when seconds matter.
Provide ongoing security training
Human error contributes to 68% of data breaches, making employee training one of your most impactful security measures. Team members serve as both your greatest vulnerability and most vigorous defense, depending on how well they understand security protocols.
Effective training sessions should cover:
- Recognizing phishing emails and social engineering attempts
- Reporting suspicious visitors or activities
- Following data handling procedures for sensitive information
- Responding appropriately to security alerts
- Using access control systems and proper badge protocols
- Avoiding tailgating at secure doors
Training works best when it is practical, relevant to specific roles, and updated regularly to address evolving threats. A culture of security awareness multiplies the effectiveness of every technological investment.
Gable's visitor management automates screening, sends real-time alerts, and keeps audit-ready logs without adding work to your front desk team.
Explore Gable Visitors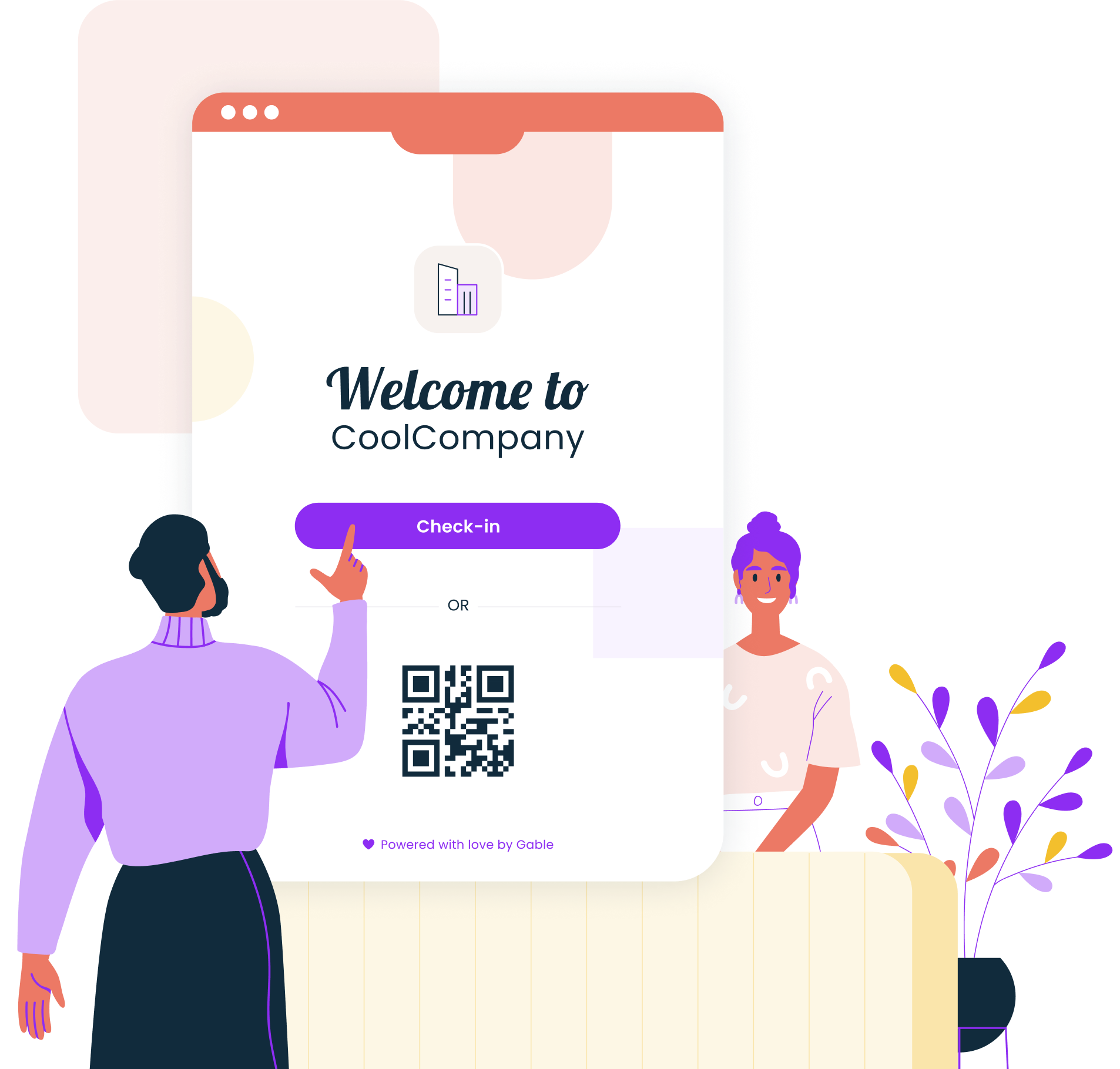
Addressing hybrid work security challenges
Hybrid work models create unique vulnerabilities that traditional security approaches cannot address. With office attendance fluctuating daily, you cannot rely on employees to notice unauthorized individuals or unusual activities.
Modern security measures must provide data-driven visibility regardless of occupancy:
- Access control systems track actual building occupancy and identify anomalies
- Visitor management protocols maintain records of all guests, even when reception staffing varies
- Integrated solutions send real-time alerts about suspicious activity without constant human monitoring
Effective hybrid workplace security combines physical measures with robust cyber threat protection, including VPNs, endpoint security, and training that covers both in-office and remote scenarios.
Integrating security solutions for maximum protection
The most effective security measures work together as an integrated ecosystem rather than standalone systems. When access control, visitor management, surveillance cameras, and alarm systems share data and coordinate responses, they provide superior protection with reduced administrative burden.
Integration enables sophisticated security scenarios. When a visitor checks in, the system automatically grants temporary access permissions. If someone attempts to access restricted zones, security personnel receive immediate alerts while cameras capture footage. These connected responses happen automatically, saving time while closing security gaps.
Workplace security policies and procedures should document how integrated systems work together. Property managers and building owners benefit from unified dashboards showing building occupancy, recent access events, active alerts, and surveillance feeds across multiple locations.
Creating a security-focused culture
Technology and policies alone cannot create a secure workplace. Building a culture where security is everyone's responsibility requires leadership commitment and employee engagement. When team members view security as a shared priority rather than someone else's job, protection improves dramatically.
Regular communication about potential threats, clear reporting procedures, and recognition for security-conscious behavior reinforce vigilance. Creating an environment where employees feel comfortable reporting suspicious activities helps identify vulnerabilities before they are exploited.
Leaders must model the behavior they expect. When executives follow security protocols consistently and treat security investments as strategic priorities, they signal that protecting employees and assets is genuinely essential.
See how Gable brings visitor management, access insights, and space data together so you can protect your people without juggling five different tools.
Get a demo





.svg)





.svg)

























