Paper sign-in sheets and manual visitor logs are creating security gaps that modern workplaces can't afford. With 74% of organizations struggling with unauthorized visitors and data breaches costing an average of $4.88 million, the visitor management process has become a critical component of workplace security and operational efficiency.
The visitor management system market reached $1.87 billion in 2024 and is projected to grow at 13.4% annually through 2030. This growth reflects a fundamental shift: organizations are recognizing that effective visitor management systems do more than track who walks through the door. They protect sensitive data, ensure compliance, and create professional first impressions that reflect your brand.
This guide breaks down the key features of a visitor management system that workplace leaders should prioritize, from security essentials to experience-enhancing capabilities that set modern solutions apart.
What is a visitor management system?
A visitor management system (VMS) is software designed to track, monitor, and control the flow of visitors within an organization. Modern visitor management is the complete process of managing everyone who enters your workplace, from the moment they pre-register for their visit to the moment they check out.
Unlike traditional paper logbooks, a modern visitor management system integrates with access control systems, automatically sends host notifications, captures visitor information digitally, and provides real-time visibility into who's on-site. The visitor management process encompasses visitor registration, identity verification, badge printing, access permissions, and detailed audit trails that support both security protocols and compliance requirements.
For organizations managing multiple locations, a centralized management approach through cloud-based visitor management software ensures consistent security standards while providing valuable insights into visitor traffic across all sites.
Why visitor management system features matter for workplace security
The stakes for workplace security have never been higher. According to IBM's 2024 research, the global average cost of a data breach reached $4.88 million, with breaches in the United States averaging $9.36 million. Physical security incidents are also rising, with 25% of businesses reporting increases in 2023 and 87% predicting that trend will continue.
Visitor management system features directly address these security risks. A visitor management system serves as your first line of defense by screening visitors before they reach sensitive areas, maintaining detailed records for compliance purposes, and enabling rapid response to security incidents through real-time alerts.
The connection between physical and digital security is critical. Organizations can't protect their data if they can't control who enters their facilities. An effective visitor management system enhances security by creating multiple verification layers that prevent unauthorized access attempts while maintaining a welcoming environment for legitimate visitors.
For workplace security policies and procedures to be effective, they need technology that consistently enforces them. Manual processes leave too much room for human error, and with 88% of cybersecurity breaches involving human mistakes, automation through visitor management software becomes essential.
Essential Visitor Management System Features
Visitor pre-registration and scheduling
The features of a visitor management system should be in place before visitors arrive. Visitor scheduling capabilities allow hosts to invite guests in advance, capture visitor information, and send arrival instructions that include directions, parking details, and security requirements.
Pre-registration eliminates the check-in bottleneck. When visitors arrive, the system recognizes them instantly, reducing wait times and creating a more professional experience. For high-volume days or events, bulk visitor invites streamline coordination and ensure appropriate personnel are prepared.
This capability also strengthens security by screening visitors against watchlists before arrival, flagging potential concerns before they become problems.
Digital visitor check-in process
The visitor check-in process sets the tone for the entire visit. Self-service kiosks or mobile apps enable visitors to complete registration quickly without requiring constant attention from front desk staff.
A streamlined check-in process typically includes completing a digital form, capturing photos for identification, signing an NDA or a document, and automatically printing a badge. The entire process can take under 60 seconds with properly configured visitor management software.
Contactless check-in options have become standard, allowing visitors to scan QR codes from their invitation emails or use mobile check-in to minimize physical contact while maintaining security protocols.
Identity verification and visitor badges
Visitor photo capture and ID scanning verify that visitors are who they claim to be. Modern systems compare visitor information against watchlists and can integrate with background check services for enhanced screening.
Visitor badges serve multiple security functions. They provide visual identification for security personnel, display access permissions, and include time stamps or QR codes that integrate with badge access control systems. Different badge designs can distinguish visitor types, making it easy to identify contractors, delivery personnel, or VIP guests at a glance.
Host notifications and real-time alerts
Instant notifications eliminate the frustrating wait time that often occurs between a visitor's arrival and a host's greeting. When visitors check in, the system automatically notifies the host via email, Slack, Microsoft Teams, or mobile app notifications.
Beyond arrival alerts, effective visitor management systems generate real-time security alerts for potential threats. If a visitor triggers a watchlist match or attempts to access restricted areas, security personnel receive immediate notification to respond appropriately.
This alert security personnel feature transforms your visitor management platform into an active security tool rather than a passive record-keeping system.
Access control integration
A visitor management system that integrates with your existing access control infrastructure provides comprehensive physical security. Visitors can receive temporary access permissions tied to specific areas and time windows, ensuring they can only enter spaces relevant to their visit.
This integration eliminates the security risks of generic visitor badges while reducing administrative burden. Temporary access automatically expires when visits conclude, preventing lingering credentials from creating vulnerabilities.
For organizations with sensitive facilities, access control integration ensures that visitor management integrates seamlessly with alarm systems, surveillance cameras, and door access systems.

See how leading organizations protect their workplaces with streamlined check-ins, automated screening, and real-time security insights that keep visitors and employees safe.
Learn more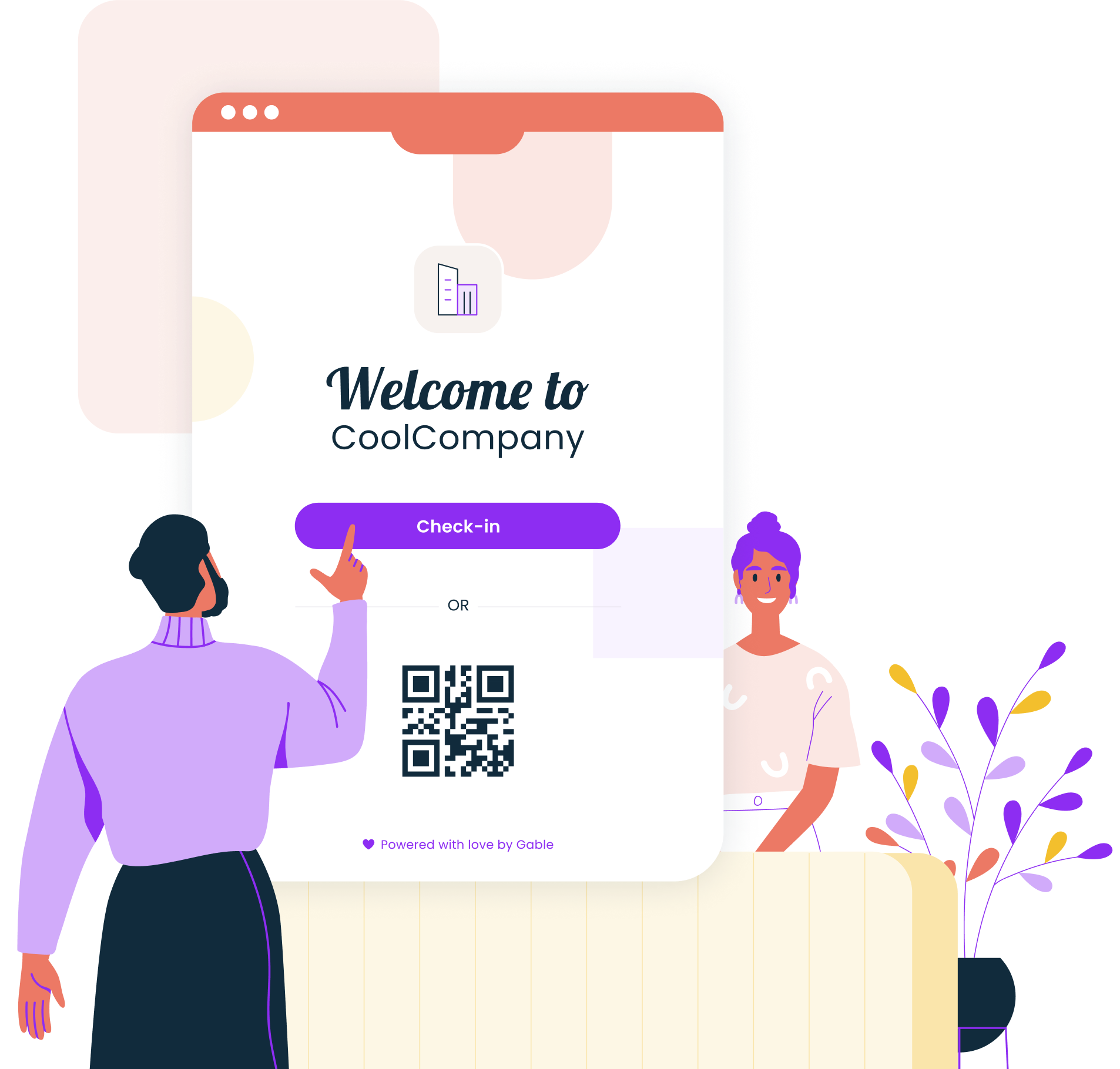
Features that enhance the visitor experience
Customizable visitor registration flows
Different visitor types require different information. A robust visitor management platform allows you to create custom check-in flows based on visit purpose, such as interviews, client meetings, contractor work, or delivery personnel.
Interview candidates might complete basic identification, while contractors sign safety waivers and provide proof of insurance. This customization ensures you collect necessary visitor information without burdening guests with irrelevant questions.
Branded welcome screens that display your company logo and colors create a professional first impression. Research shows that 40% of people report their perception of a company has been negatively affected by their experience in the corporate lobby. A polished digital check-in experience signals that your organization values attention to detail.
Multi-location support and centralized management
For organizations operating across multiple locations, centralized management capabilities ensure consistent visitor management processes across all locations. Administrators can configure security protocols, visitor types, and compliance requirements from a single dashboard while allowing location-specific customization where needed.
This approach maintains brand consistency and security standards while accommodating local requirements. Visitor data aggregates across sites, providing insights into traffic patterns and enabling comparison of visitor activity across your entire portfolio.
Cloud-based system architecture makes this possible without requiring on-premise servers at each location, reducing IT burden while improving reliability and security.
Emergency preparedness features
Knowing exactly who's in your building at any moment is critical during emergencies. Visitor tracking capabilities provide real-time headcounts that help security personnel and first responders account for everyone during evacuations.
Emergency notification features can broadcast alerts to all checked-in visitors simultaneously, providing evacuation instructions or shelter-in-place guidance. Detailed visitor logs support post-incident analysis and compliance documentation.
Integration and analytics
Workplace system integrations
A visitor management solution that works in isolation creates data silos and workflow friction. Look for systems that integrate with your existing technology stack, including calendar applications (Google Calendar, Microsoft Outlook), communication tools (Slack, Microsoft Teams), HR systems (Workday, Rippling), and building management platforms.
These integrations automate workflows that would otherwise require manual intervention. Calendar integrations can automatically generate visitor invitations when meetings are scheduled with external participants. Communication integrations ensure hosts receive notifications through channels they actually monitor.
Visitor analytics and reporting
The visitor data captured by your visitor management system represents a valuable resource for operational optimization. Generate detailed reports on visitor volume, peak visitor hours, average visit duration, and popular visit purposes.
This real-time visitor data supports data-driven decisions about front desk staffing, security resource allocation, and space planning. Understanding visitor traffic patterns helps facilities teams prepare for high-volume periods and identify opportunities to improve operational efficiency.
For compliance purposes, audit trails document every visitor interaction, supporting regulatory requirements and internal security reviews. The ability to quickly search and export visitor records simplifies response to audits or investigations.
Compliance and data protection
Visitor management systems store data that includes names, contact information, photos, and potentially sensitive business details. GDPR compliance, HIPAA requirements, and other privacy regulations impose strict requirements on how this information is collected, stored, and protected.
According to DLA Piper's 2024 GDPR report, organizations faced over €1.2 billion in privacy-related fines in 2024 alone. Effective visitor management software includes built-in consent management, data retention controls, and secure storage that help organizations maintain compliance while collecting necessary visitor information.
Look for systems that offer configurable data retention periods, visitor consent acknowledgment during check-in, and secure data handling practices that align with your compliance obligations.
Get a comprehensive framework for visitor registration, access control, and compliance requirements to protect your people and data.
Read the guide
How to choose the right visitor management system
Selecting the right visitor management system requires matching features to your specific operational needs. Start by mapping your visitor types, whether clients, candidates, contractors, or delivery personnel, and identify the different security requirements and information needs for each.
Consider your growth trajectory. A system that works for a single office may not scale effectively to multiple locations. Cloud-based visitor management solutions typically offer better scalability than on-premise alternatives.
Integration capabilities often determine long-term success. The most feature-rich system provides limited value if it can't connect with your existing tools. Prioritize solutions that offer pre-built integrations with your current technology stack and APIs for custom connections.
Evaluate the visitor experience from your guests' perspective. Test the check-in flow yourself. Is it intuitive? How long does registration take? Can visitors complete the process without assistance? A secure environment matters, but so does creating a welcoming experience that reflects your organizational values.
Finally, consider the vendor's approach to updates and support. Workplace security requirements evolve continuously. Choose a visitor management solution backed by a vendor committed to ongoing development and responsive customer support.
Effective visitor management has evolved from a simple administrative task into a strategic capability that protects your people, supports compliance, and creates a professional first impression. The key features of a visitor management system outlined above provide a framework for evaluating solutions. Still, the right choice depends on your specific security requirements, integration needs, and growth plans.
Organizations that invest in comprehensive visitor management platforms gain more than security benefits. They gain valuable insights into visitor patterns, operational efficiencies from automated workflows, and the peace of mind that comes from knowing exactly who's in their facilities at any moment.
Ready to enhance visitor experience while strengthening security? Our team will show you how Gable Visitors handles everything from pre-registration to analytics.
Get a demo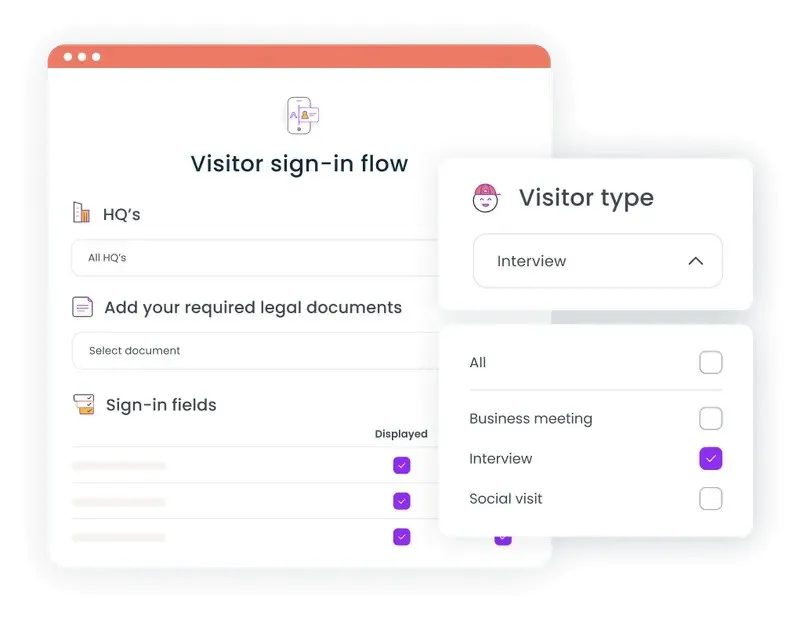





.svg)





.svg)

























